
***************************************************************************
* Description: Created self-signed certificate for WebLogic managed server
* Date: 11:44 AM EST, 03/02/2021
***************************************************************************
<1> After creating domain and managed server, the admin server & managed server's HTTPS port is assigned with an WebLogic integrated Demo Certs:
|
|__ o. Those Demo certs could not be used in production environment, and vulnerbility scan will be alerting this as well.
|
|__ o. If CA certificates could not be purchased, a self-signed certificate is recommanded.
<2> Several utilities could create self-signed certificate, and in this case, KEYTOOL is preferred:
|
|__ $ which keytool
/usr/java/jdk1.8.0_261-amd64/bin/keytool
<3> Creating a Key Pair in a key store, and a .jks keystore file will be created physically:
|
|__ $ keytool -genkey -keyalg RSA -alias snflwr -keystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks \
-dname "CN=`hostname`, OU=HHS, O=HHS, L=Rockville, ST=MD, C=US" -storepass Oracle2019 -validity 3600 -keysize 2048 -keypass Oracle2019
Warning: The JKS keystore uses a proprietary format.
It is recommended to migrate to PKCS12 which is an industry standard format using
"keytool -importkeystore -srckeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks \
-destkeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks -deststoretype pkcs12".
<4> Creating a self-signed identity certificate, and saved in the keystore. The certificate info will be saved in physical keystore file as well:
|
|__ $ keytool -selfcert -v -alias snflwr -keypass Oracle2019 -keystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks \
-storepass Oracle2019 -storetype jks -validity 3600
New certificate (self-signed):
[
[
Version: V3
Subject: CN=suflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
params: null
modulus: 2088893171860531144544091571977442900781920883519
public exponent: 65547
Validity: [From: Thu Feb 25 10:50:57 EST 2021,
To: Sat Jan 04 10:50:57 EST 2031]
Issuer: CN=suflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
SerialNumber: [ 01bad90f]
Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 3A EF 13 C3 95 5B 21 80 53 A7 A6 09 23 E8 09 9A :....[!.S...#...
0010: 5D D5 3B 61 ].=a
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 53 95 6D 87 DF C4 67 25 DD F7 B2 DE E7 8D 1C 51 S.m...g%.......Q
0010: 20 B8 37 B5 27 00 05 0A 44 99 80 00 57 C3 ED 57 .7.'...D...W..W
0020: 80 50 57 70 F0 F0 54 32 A4 A7 CB 69 98 F1 D7 10 .PWp..T2...i....
0030: C8 CD C4 A0 03 8C 66 30 3F 1A 2B 68 06 D1 CE 00 ......f0?.+h....
0040: 99 2D 00 A7 7F 52 CC 5F 67 09 D2 D4 F0 3D 7E EE .-...R._g....=..
0050: 9A 43 1C 03 D1 6D 0B E9 5E 9E FA 66 FB 69 79 18 .C...m..^..f.iy.
0060: 34 5D 30 09 7D C3 CB 79 F7 61 7E 6E CA CD 13 EE 4]0.N..T.a.n....
0070: BE 64 21 2D 73 AF 6C 99 5C B9 C0 76 DB 1E 3A 25 .d!-s.l.\..v..:%
0080: 6F BB D8 79 D5 CE D2 E4 29 44 32 BA 02 EC E2 EC o..N....)D2.....
0090: 4E 11 51 EB 08 C8 3D F6 CC 9B 33 66 6C 1B D7 90 N.Q...=...3fl...
00A0: 24 F2 0E 0A 2D B9 09 63 77 C1 0D 44 78 50 4C E5 $...-..cw..DxPL.
00B0: 85 6A 65 10 56 D0 C5 3F CA 1C 15 28 21 DE 68 CE .je.V..?...(!.h.
00C0: 63 48 59 E8 CC D3 ED 44 5C F8 9A 28 B0 5E E8 64 cHY....D\..(.^.d
00D0: 0C 51 FA 4A 43 71 FD 55 98 75 4C 6F AC AB 38 47 .Q.JKq.U.uLo..8G
00E0: 7D F5 95 F0 41 0C D3 07 DA 73 20 E7 B5 6D 1C 85 ....A....s ..m..
00F0: B1 6D CE 12 A2 38 4B B8 23 AD 3A 12 65 95 EF 1B .m...8K.#.:.e...
]
[Storing /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks]
Warning:
The JKS keystore uses a proprietary format.
It is recommended to migrate to PKCS12 which is an industry standard format using
"keytool -importkeystore -srckeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks \
-destkeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks -deststoretype pkcs12".
<5> Export the identity certificate, from keystore, into a physical file with extension .der:
|
|__ $ keytool -export -v -alias snflwr -file "`hostname`-rootCA.der" \
-keystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks -storepass Oracle2019
Certificate stored in file
Warning:
The JKS keystore uses a proprietary format.
It is recommended to migrate to PKCS12 which is an industry standard format using
"keytool -importkeystore -srckeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks \
-destkeystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks -deststoretype pkcs12".
You have mail in /var/spool/mail/oracle
<6> Import the same self-signed identity certificate into trust keystore as a ROOT certificate, simutenously, it will create trust keystore as physical file trust.jks:
|
|__ $ keytool -import -v -trustcacerts -alias snflwr \
-file "/u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/`hostname`-rootCA.der" \
-keystore /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/trust.jks -storepass Oracle2019 -noprompt
Certificate was added to keystore
[Storing /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/trust.jks]
<7> Configure SSL for the managed server via WebLogic console:
|
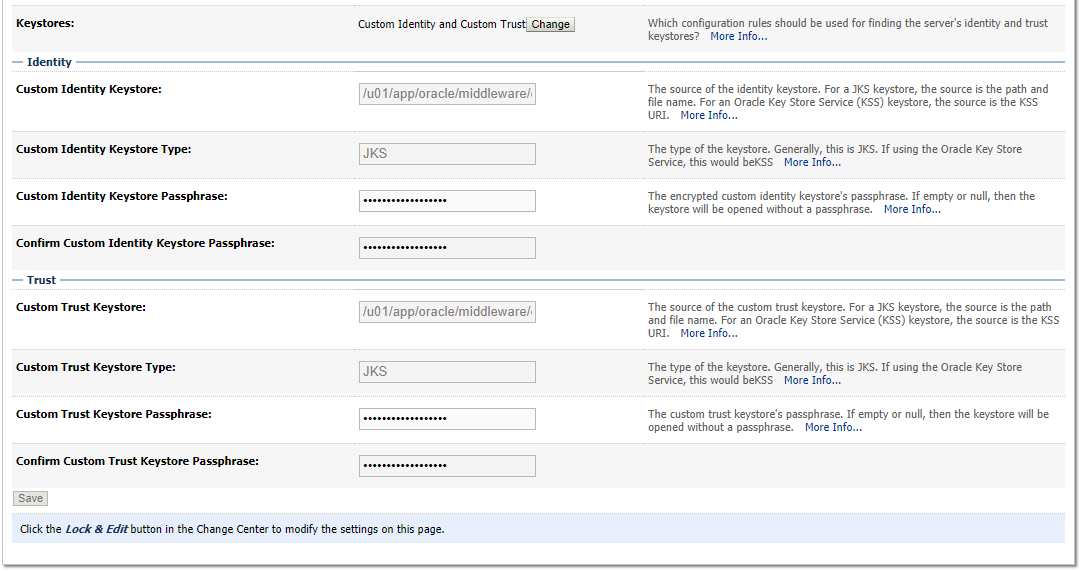
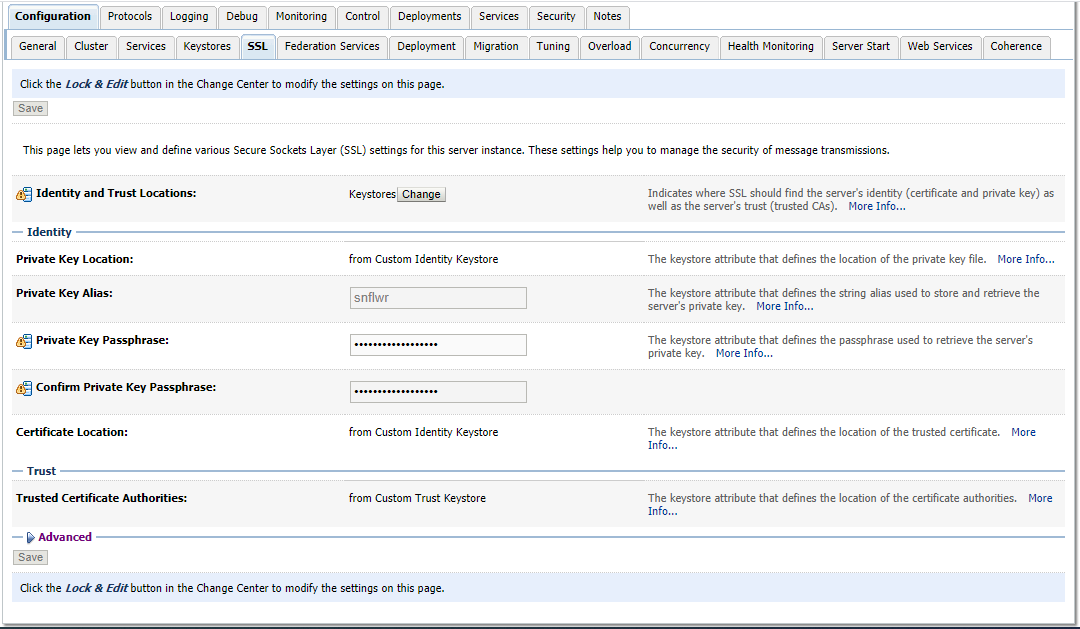
|__ o. Domain Structure => Servers => => Keystores => Click on "Change" => To "Custon Identify and Custon Trust" => Go to Tab "SSL" to give alias & Key Passphrase:
 <8> Add below info into Node Manager config file, otherwise Admin Server could not communicate with Managed Server via Node Manager:
|
|__ o. /u01/app/oracle/middleware/config/user_projects/domains/pmisd/nodemanager/nodemanager.properties
KeyStores=CustomIdentityAndCustomTrust
CustomIdentityKeystoreType=jks
CustomIdentityKeyStoreFileName=/u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks
CustomIdentityKeyStorePassPhrase=Oracle2021
CustomIdentityPrivateKeyPassPhrase=Oracle2021
CustomIdentityAlias=snflwr
CustomTrustKeystoreType=jks
CustomTrustKeyStoreFileName=/u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/trust.jks
CustomTrustKeyStorePassPhrase=Oracle2021
<9> But, following error comes up, when starting Managed Server via OEM "unable to find valid certification path to requested", but can boot it via command line:
|
|__ o. The reason is since the WebLogic domain or servers are running based on the Java on OS level /usr/bin/java, not Oracle Fusion Middleware integrated Java.
|
|__ o. So, the cert needs to be imported into OS Java Keystore as well by root user:
|
|__ $ sudo keytool -importcert -keystore /usr/java/jdk1.8.0_261-amd64/jre/lib/security/cacerts -storepass changeit \
-file /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/snflwr.emeralit.com-rootCA.der -alias "snflwr"
Enter keystore password:
Owner: CN=snflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
Issuer: CN=snflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
Serial number: 1bad90f
Valid from: Thu Feb 25 10:50:57 EST 2021 until: Sat Jan 04 10:50:57 EST 2031
Certificate fingerprints:
MD5: A7:87:AC:32:D0:B1:8B:92:4C:50:98:97:34:08:E0:19
SHA1: DE:A5:3D:7E:5B:20:B0:C8:96:B3:F6:6D:1F:71:5D:C4:16:DD:6F:19
SHA256: 7D:D7:14:16:D7:5D:E9:6F:33:5D:ED:0A:4D:22:1B:53:67:B7:28:37:F2:FB:16:3F:B5:1B:0A:06:A5:A8:E9:D3
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 3A EF 13 C7 95 5B 21 80 58 A7 A1 09 43 E8 09 9A :....[!.S...#...
0010: 5D D5 3D 61 ].=a
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Reference:
|
|__ o. https://oracle-base.com/articles/11g/weblogic-configure-ssl-for-a-managed-server
<8> Add below info into Node Manager config file, otherwise Admin Server could not communicate with Managed Server via Node Manager:
|
|__ o. /u01/app/oracle/middleware/config/user_projects/domains/pmisd/nodemanager/nodemanager.properties
KeyStores=CustomIdentityAndCustomTrust
CustomIdentityKeystoreType=jks
CustomIdentityKeyStoreFileName=/u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/identity.jks
CustomIdentityKeyStorePassPhrase=Oracle2021
CustomIdentityPrivateKeyPassPhrase=Oracle2021
CustomIdentityAlias=snflwr
CustomTrustKeystoreType=jks
CustomTrustKeyStoreFileName=/u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/trust.jks
CustomTrustKeyStorePassPhrase=Oracle2021
<9> But, following error comes up, when starting Managed Server via OEM "unable to find valid certification path to requested", but can boot it via command line:
|
|__ o. The reason is since the WebLogic domain or servers are running based on the Java on OS level /usr/bin/java, not Oracle Fusion Middleware integrated Java.
|
|__ o. So, the cert needs to be imported into OS Java Keystore as well by root user:
|
|__ $ sudo keytool -importcert -keystore /usr/java/jdk1.8.0_261-amd64/jre/lib/security/cacerts -storepass changeit \
-file /u01/app/oracle/middleware/config/user_projects/domains/pmisd/servers/Sunflower/keystore/snflwr.emeralit.com-rootCA.der -alias "snflwr"
Enter keystore password:
Owner: CN=snflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
Issuer: CN=snflwr.emeralit.com, OU=DDS, O=DDS, L=McLean, ST=VA, C=US
Serial number: 1bad90f
Valid from: Thu Feb 25 10:50:57 EST 2021 until: Sat Jan 04 10:50:57 EST 2031
Certificate fingerprints:
MD5: A7:87:AC:32:D0:B1:8B:92:4C:50:98:97:34:08:E0:19
SHA1: DE:A5:3D:7E:5B:20:B0:C8:96:B3:F6:6D:1F:71:5D:C4:16:DD:6F:19
SHA256: 7D:D7:14:16:D7:5D:E9:6F:33:5D:ED:0A:4D:22:1B:53:67:B7:28:37:F2:FB:16:3F:B5:1B:0A:06:A5:A8:E9:D3
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 3A EF 13 C7 95 5B 21 80 58 A7 A1 09 43 E8 09 9A :....[!.S...#...
0010: 5D D5 3D 61 ].=a
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Reference:
|
|__ o. https://oracle-base.com/articles/11g/weblogic-configure-ssl-for-a-managed-server
Your Comments